Is it the Beginning of the End of Passwords?
In the wake of cyber-attacks at some of the biggest Superannuation Funds in Australia last week, one question should be asked, is this the beginning of the end of Passwords? The safety of using Passwords has been broken for a long time. Managing passwords can be dauntingly challenging. They can be difficult to remember, and often, people reuse them across multiple platforms and systems, which makes them a target for cybercriminals. In fact, according to the 2023 Verizon Data Breach Investigations Report (DBIR), over 50% of data breaches are linked to stolen or compromised credentials. This exposes sensitive data, whether it’s banking details, emails, or personal information, to potential risks.
Last week cyber-attacks of those Australian Superannuation Funds are clearly the evidence of these issues.
Are Passkeys safer than Passwords?
To address these above issues, passkeys offer a more secure alternative to traditional passwords. Passkeys are meant to replace Passwords. The main reason of using Passkeys is eliminating the need to memorise password, reduce the user friction and complexity. Organisations are gradually adopting Passkeys, rather than replacing them in such Big-Bang approach. In the End, Passwords might still be around for legal reasons.
Passkeys use cryptographic key pairs. These digital keys are unique, secure, and tied to a specific service, much like the key to your house. Passkeys operate through FIDO2, a set of standards developed by the FIDO Alliance, eliminating the need for traditional passwords. Instead of typing in a password, you authenticate using a device (with optional biometrics), providing a far more secure and convenient solution. The Private Key stays on your devices, never shared online by any platforms. They cannot be copied, reused, making them very strong resistant to phishing and thief. Hence, Passkeys are much safer than Passwords.
Why do We need Facial Biometrics in addition to using Passkeys?
Facial recognition offers enhanced level of security, as it is difficult to replicate or steal someone’s face, compare to stealing Passwords or PINs.
How do Facial biometrics work?
- Detection: The app detects your face from your physical location, at the time you are using the app.
- Capture: Device camera sensors capture your face in 3D metrics
- Conversion: using various algorithms, the facial captured data is mathematically converted based on your facial features.
Do we authenticate the User? Or the Device?
At present, the on-device biometric authentication is not directly bound to someone’s real identity profile. A much better way is getting the data drawn from your face to create a private keys that prove who you really are, and when you complete your banking, or online purchases, no biometric information is saved anywhere, compare to the current model, when sensitive data have to be encrypted and saved.
What are the current gaps in implementation of Passkeys?
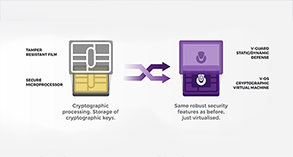
Most implementations store the FIDO private key in the Keystore/Keychain, which may not be deemed secure enough, especially if the keys are not stored in a Trusted Execution Environment (TEE). Even if the phone has a TEE (such as Secure Enclave), there is a general flaw in the architectural design which hackers can exploit. We call this design flaw the Trust Gap because the TEE has no way of determining the identity of the app and relies on the OS to do so. If the OS is compromised, the keys in the TEE can also be misused. This is an insidious and sophisticated attack as the targeted app does not even need to be running or be tampered with to be compromised.
Some passkey implementations also synchronise the authentication private key to the cloud, so that the user can restore his keys when he logs in to a new phone. This means that the security of these passkeys becomes equivalent to the security of the phone manufacturer’s ID. In such cases, the level of security becomes dependent on the underlying cloud account used for backup and recovery.
Financial institutions cannot accept that banking authentication security becomes reduced to the security of phone manufacturer’s ID. Neither will phone manufacturers accept any liability due to security breaches.
How do V-Key overcome those Gaps/Issues?
V-Key ID’s implementation of FIDO passkeys uses the V-OS Virtual Secure Element to protect private keys. V-OS is like a virtual TEE that provides a secure environment for cryptographic keys. Unlike the phone’s TEE, V-OS is not vulnerable to the Trust Gap issue because of how it is tightly bound to the app and its ability to scan for app tampering and runtime attacks. With V-Key ID, the V-OS protected passkeys also do not need to be synchronized to the cloud as fresh keys can be created when the user logs in with his face to a new device. This unique combination of privacy-enabled facial biometrics and a secure passkey vault (V-OS) positions V-Key ID well as the future of mobile authentication.
V-Key ID: Taking Security to the next level
At V-Key, we go beyond just passkeys by integrating advanced security layers like V-OS, ZeroMap, and ZeroBiometrics™ into our V-Key ID solution, enhancing mobile authentication. This approach ensures every mobile interaction is securely protected, providing a more effective and reliable passwordless experience. Whether logging into a mobile banking app or completing an online transaction, V-Key ID guarantees that only you can access your account, using something uniquely yours—your biometrics.
A short video of Empowering the Digital Journey with our V-Key ID, a revolutionary solution that goes beyond fragmented authentication, offering a safer, more robust approach to safeguarding your digital life, can be found Here.
By combining privacy-preserving biometrics, secure data encryption, and seamless user verification, V-Key ID establishes a new benchmark in mobile security. It offers users the convenience and confidence they need to protect their digital identity without compromising their data.
With V-Key ID, FIDO2 standards are seamlessly implemented, providing a robust and secure authentication process that enhances security compared to traditional password-based methods. Businesses adopting this technology can offer their customers a more seamless and secure online experience, eliminating the risks associated with passwords.
Ready to move beyond passwords?
If you’re thinking about taking the next step toward stronger, simpler mobile authentication, we’d love to show you what’s possible with V-Key ID. Get in touch with our team to learn more.